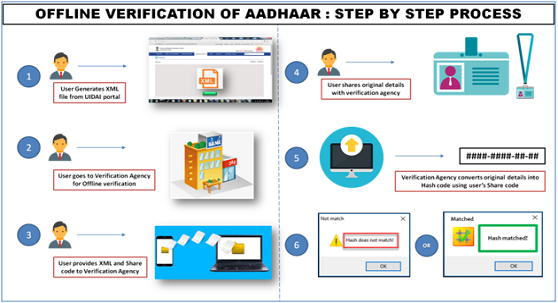
Enrolment Data Security
Enrolment Data Security
Aadhaar system is an identity system, dealing primarily with identity data.

Aadhaar defines how this data will be collected, used, retained and protected from unauthorized access. The following strategies are adopted for data Security :
- to store the minimal amount of identity data
- to stay away from maintaining transaction data
- to have federated model with well-defined rules and processes
Enrolment Data Security
The enrolment/update data packets are encrypted by the client using public key cryptography with each data record having an HMAC which can identify any integrity violation of the data. Master keys are stored and managed within HSM (Hardware Security Module) appliance.
Following should be noted:
- Every enrolment station, registrar, enrolment agency, operator, and supervisor are registered and authenticated.
- Every packet is biometrically signed by operator (and supervisor in various cases) and contains complete process data including station ID, timestamp, location (pin code, GPS). This allows strong validations and traceability at packet level.
- Every enrolment data packet is “always” stored in encrypted, tamper-evident files and are never decrypted or accessed during transit.
- Enrolment data is “never” decrypted until it is reached within UIDAI’s data centre’s secure production zone.
Usage of strong 2048-bit PKI encryption technologies ensures that no agencies or persons can access, modify, or misuse the resident data during field enrolment or in transit to the UIDAI data centres.
In addition to enrolment packet, resident data in Aadhaar master database and BI data store is protected through various security measures. These include:
- Encryption – Ensures data is encrypted and not available to administrators and other users in plain text format.
- Anti-Tampering – Ensures data is only altered by authorized applications and not via command line SQL scripts.
- Data Partitioning - Data is partitioned and stored across multiple databases with a random alias being the only link to ensure there is no central database table where all resident data is available.
- Anonymization – Hashing techniques are used for anonymizing data in BI/Reporting data store, and yet retaining the ability to do analytics.
Other than application techniques as described above to protect resident data, UIDAI has implemented data centre best practices and technologies such as firewalls, IPS systems, zoning and access control, centralized security policy management, audits, 24x7 monitoring through Security Operations Centre (SoC), and strong security procedures used to ensure CIDR is protected.












 play_circle_outline
play_circle_outline
 play_circle_outline
play_circle_outline
 play_circle_outline
play_circle_outline
 play_circle_outline
play_circle_outline
 play_circle_outline
play_circle_outline